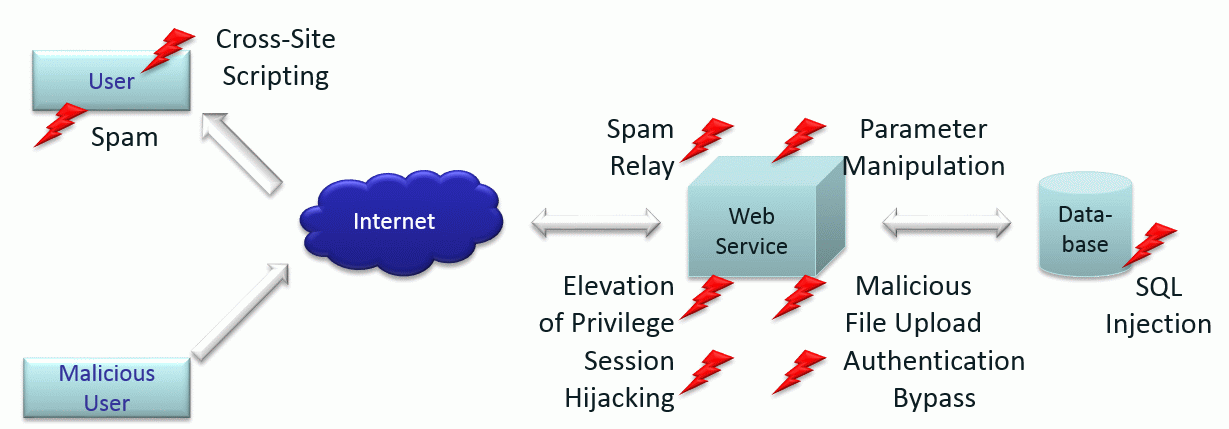
Secure software continues to function as intended even if under malicious attack.
Software engineering is about the development of software with high quality and under economic conditions. High-quality comprises the fulfillment of non-functional requirements like reliability, robustness, maintainability, safety, and last but not least, security. Secure software continues to function as intended even if under malicious attack.
The importance of IT security is out of doubt. Data, computer and network security are essential for any business or organization. Software security often remains out of focus, from an organization’s, a developer’s and from an end-user’s point of view. Software security comprises security bugs, security flaws, mitigation issues, security development, etc.
Publications
M. Riegler, J. Sametinger, M. Vierhauser, M. Wimmer: A Model-based Mode-switching Framework based on Security Vulnerability Scores, Journal of Systems and Software, Volume 200, June 2023.
Doi: 10.1016/j.jss.2023.111633 Journal Article
M. Riegler, J. Sametinger, Rozenblit: Context-aware Security Modes for Medical Devices, Annual Modeling and Simulation Conference ANNSIM’22, San Diego, CA, USA, July 18-20, 2022, pp. 372-382.
Doi: 10.23919/ANNSIM55834.2022.985928
Conference Article
A.S. Nasser, M. Riegler, J. Rozenblit: Towards Strategies for Secure Data Transfer of IoTDevices with Limited Resources, 33rd DEXA Conferences and Workshops, Dexa 2022, Vienna Austria, August 22-24.2022.
Doi: 10.1007/978-3-031-14343-4_30 Conference Article
M. Riegler, J. Sametinger, Ch. Schönegger: Mode-Switching for SecureEdge Devices, 33rd DEXA Cconferences and Workshops, Dexa 2022, Vienna, Austria, August 22-24, 2022.
Doi: 10.1007/978-3-031-14343-4_32 Conference Article
F. Berner, J. Sametinger: Information Disclosure Detection in Cyber-Physical Systems, IWCFS 2019 - 3rd International Workshop on Cyber-Security and Functional Safety in Cyber-Physical Systems, Linz, Austria, August 26-29, 2019,
DOI: 10.1007/978-3-030-27684-3_12
Workshop Article
A. Rao, N. Carreón, R. Lysecky, J. Rozenblit, J. Sametinger: Resilient Security of Medical Cyber-Physical Systems, IWCFS 2019 - 3rd International Workshop on Cyber-Security and Functional Safety in Cyber-Physical Systems, Linz, Austria, August 26-29, 2019.
DOI: 10.1007/978-3-030-27684-3_13 Workshop Article
J. Sametinger: Securing Smart Homes, IWCFS 2019 - 3rd International Workshop on Cyber-Security and Functional Safety in Cyber-Physical Systems, Linz, Austria, August 26-29, 2019.
DOI: 10.1007/978-3-030-27684-3_14 Workshop Article
A. Rao, J. Rozenblit, R. Lysecky, and J. Sametinger, Trustworthy Multi-Modal Framework for Life-Critical System Security, in Proceedings of the Annual Simulation Symposium (ANSS '18), Baltimore, MD, USA, April 15-18, 2018
https://dl.acm.org/citation.cfm?id=3213049 Conference Article
M. Biro, A. Mashkoor, J. Sametinger, and R. Seker, “Guest Editors’ Introduction: Special Issue on Software Safety and Security Risk Mitigation in Cyber-physical Systems,” IEEE Software, vol. 35, no. 1, pp. 24–29, January/February 2018.
Guest Editors' Introduction
Misc
M. Riegler, J. Sametinger: Embedded Web Device Security, The Eighth International Conference on Emerging Security Information, Systems and Technologies, SECUREWARE, Lisbon, Portugal, November 16 - 20, 2014.
Conference Article
A. Wagner, J. Sametinger, Using the Juliet Test Suite to compare Static Security Scanners, 11th International Conference on Security and Cryptography (SECRYPT 2014) Vienna, Austria - August 28-30, 2014.
DOI: 10.5220/0005032902440252
Conference Article
R. Maier, J. Sametinger: Profiles for Convenient Front-end Privacy, SEKE 2013, 25th International Conference on Software Engineering and Knowledge Engineering, Boston USA, June 27-29, 2013.
Conference Article
J. Sametinger: Software Security , IEEE ECBS 2013, 20th Annual IEEE International Conference and Workshops on the Engineering of Computer Based Systems (ECBS), Phoenix AZ, 22-24 April 2013.
DOI: 10.1109/ECBS.2013.24
Conference Article
R. Schlöglhofer, J. Sametinger: Secure and Usable Authentication on Mobile Devices, MoMM2012 - 10th International Conference on Advances in Mobile Computing & Multimedia, Bali, Indonesia, December 22-26, 2012.
DOI: 10.1145/2428955.2429004
Conference Article
M. Kern, J. Sametinger: Permission Tracking in Android, UBICOMM 2012, Sixth International Conference on Mobile Ubiquitous Computing, Systems, Services and Technologies, ISBN: 978-1-61208-236-3, pp. 148-155, Barcelona, Spain, September 23-28, 2012.
Conference Article
M. Kainerstorfer, J. Sametinger, A. Wiesauer: Software Security for Small Development Teams - A Case Study, 13th International Conference on Information Integration and Web-based Applications & Services (iiWAS2011), Ho Chi Minh City, Vietnam, December 5-7, 2011.
DOI: 10.1145/2095536.2095590
Conference Article
G. Draxler, J. Sametinger, A. Wiesauer: Electronic Payment and Online Gaming, 16th International Conference on Distributed Multimedia Systems, Oak Brook, USA, October 14-16, 2010.
Conference Article
A. Wiesauer, J. Sametinger: A Security Design Pattern Taxonomy based on Attack Patterns, ICETE 2009 - International Joint Conference on e-Business and Telecommunications, Milan, Italy, July 7-10, 2009.
Conference Article
M. Meike, J. Sametinger, A. Wiesauer: Security in Open Source Web Content Management Systems, IEEE Security & Privacy, vol. 7, no. 4, pp. 44-51, 2009.
DOI: 10.1109/MSP.2009.104
Journal Article
S. Sageder, J. Sametinger, A. Wiesauer: Case Study: Using Digital Signatures for the Archival of Medical Records in Hospitals, CRiSIS 2008, 3rd International Conference on Risks and Security of Internet and Systems, Tozeur, Tunisia, October 28-30, 2008.
DOI: 10.1109/crisis.2008.4757481
Conference Article

